XML Ping of death: An attacker leverages the security functionality of the system aimed at thwarting potential attacks to launch a denial of service attack against a legitimate system user. The weakness that is being leveraged by an attacker is the very security feature that has been put in place to counteract attacks. All of the above attacks exploit the loosely coupled nature of web services, where the service provider has little to no control over the service requester and any messages the service requester sends. An attacker can leverage this throttling mechanism to lock a legitimate user out of their own account.
| Uploader: | Brashicage |
| Date Added: | 7 May 2012 |
| File Size: | 40.52 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 4954 |
| Price: | Free* [*Free Regsitration Required] |
This is, of course, most distributed systems technology including Java.
Index of /download/archive/5.20
The main weakness in XDoS is that the service provider generally must inspect, parse, and validate the XML messages to determine routing, workflow, security considerations, and so on. An attacker leverages the security functionality of the system aimed at thwarting potential attacks to launch a denial of service attack against a legitimate system user. XML Ping of death: The weakness that is being leveraged by an attacker is the very security feature that has been put in place to counteract attacks.
Net, databases, and so on.
Mikrotik Winbox Download
In other words, this is a normal flooding attack augmented by using messages that will require extra processing on the mikrptik.
All of the above attacks exploit the loosely coupled nature of web services, where the service provider has little to no control over the service requester and any messages the service requester sends.
XML allows the definition of macro-like structures that can be used to simplify the creation of complex structures. According to its self-reported version, the remote networking device is running a version of MikroTik prior to 6. Mikrotik RouterOS before 6.
DOM creates in memory representation of XML document, but when document is very large for example, north of 1 Gb service provider host may exhaust memory trying to build memory objects. XML Ping of the Death An attacker initiates a resource depletion attack where a large number of small XML messages are delivered at a sufficiently rapid rate to cause a denial of service or crash of the target.
The transactions used are immaterial as long as they cause resource utilization on the target. Many systems, for instance, implement a password throttling mechanism that locks an account after a certain number of incorrect log in attempts.
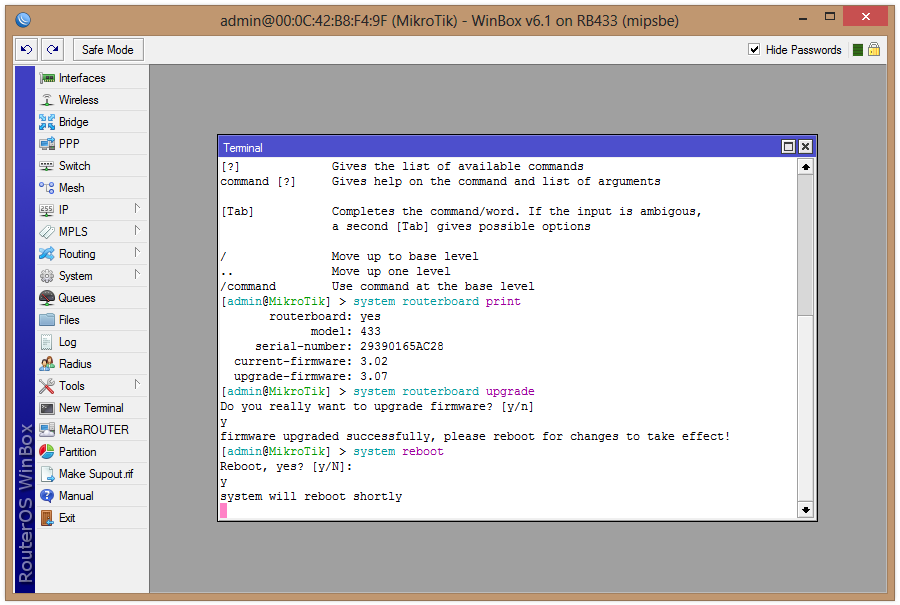
It is exactly these inspection, parsing, and validation routines that XDoS targets. Transactions such as repetitive SOAP transactions can deplete resources faster than a simple flooding attack because of the additional resources used by the SOAP protocol and the resources necessary to process SOAP messages.
MikroTik RouterOS refmap via4. Inducing Account Lockout An attacker leverages the security functionality of the system aimed at thwarting potential attacks to launch a denial of service attack against a legitimate system user.
MikroTik RouterOS , & Cracked Full Level 6 | All About Mikrotik
A small number of mi,rotik expansions can result in an exponential growth in demands on memory. However, this capability can be abused to create excessive demands on a processor's CPU and memory.
An attacker can leverage this throttling mechanism to lock a legitimate user out of their own account.

Комментариев нет:
Отправить комментарий